
Management organization
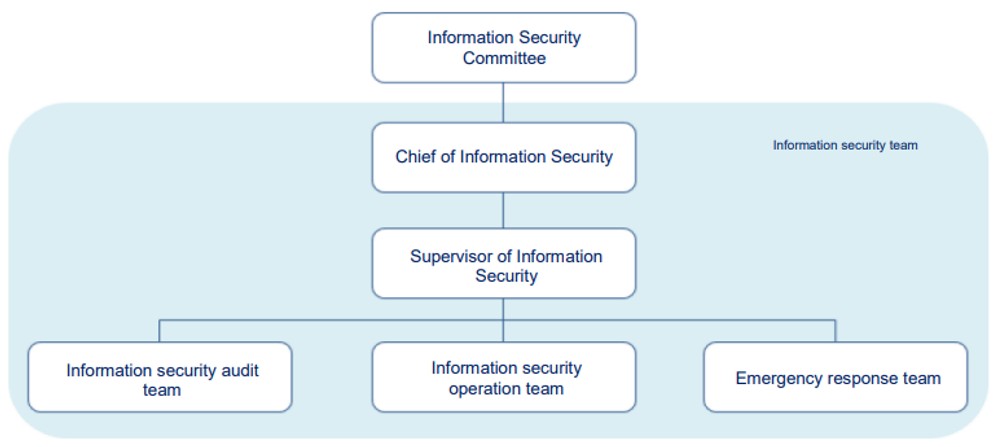
In order to enhancement the company's information security management and ensure security of its data, system, and network, an Information Security Committee has been established. The director of the information center serves as the convener of the Committee, and reports to the board of directors at least once a year. The organization of the Committee includes the information security operation team, the incident response team, and the information security audit team; The information security operation team implements the building of the Information Security Management System, including network management and system management; The incident response team is responsible for business continuity plan specifications and crisis handling procedures, implementing incident response measures and reporting, and conducting post-incident analysis and prevention; The information security audit team cooperates with the company's audit unit to conduct information security auditing, including internal and external auditing.
Information security policy
The company's information security policy aims to "maintain the confidentiality, integrity, availability, and legality of company information, and avoid human negligence, deliberate destruction, and natural disasters, which result in improper use, leakage, tampering, damage, or disappearance of information and assets which affect the company's operations and cause damage to the company's rights and interests." The company introduced the ISO27001 information management system in 2016, and has regularly obtained ISO27001 certification. The current certificate is valid from August 2022 to August 2025. Through the introduction of the ISO27001 information security management system, the ability to respond to information security incidents has been strengthened, and assets of the company and customers are more secure.
Specific information security management plan
|
Item
|
Specific management measures
|
|
Firewall protection
|
1. Set firewall connection rules.
2. Can only be opened with the approval of the responsible supervisor when there are special connection needs.
|
|
User Internet access control mechanism
|
1. Use an automatic website protection system to control users' online behavior.
2. Automatically filter users' Internet access to websites that may have links to Trojans, ransomware, or malicious programs.
|
|
Antivirus software
|
Use antivirus software and automatically update virus pattern files to reduce the chance of infection.
|
|
Updating of the operating system
|
The operating system is automatically updated. If it is not updated for some reason, the information center will assist in updating.
|
|
Email security control
|
1. There is automatic email threat scanning protection that prevents suspicious attachment files, phishing emails, spam emails, and expands the protection range against malicious links before users receive emails.
2. After a personal computer receives an email, the antivirus software also scans it for suspicious attachment files.
|
|
Data backup mechanism
|
Every important information system database is set up for daily backup.
|
|
Important file upload server
|
The important files of each department in the company are stored on this server, which is backed up and saved by the information center.
|
|
Information security insurance
|
The company's customers are mainly corporate customers, and there is no risk of consumer personal data custody. After evaluating the insurance coverage and applicable industries for IT security insurance on the market, we have not purchased capital security insurance for the time being. However, in response to the challenges faced by information security,
certain software and hardware have been imported, such as firewalls, anti-virus software, intrusion prevention systems, etc., and we continue to pay attention to the changing trends of the information environment and strengthen our employees' awareness of information security crises and the ability of information security handlers to respond to such crises.
|
Enhancement in Digital Information Security.Upgrade of Customer Privacy
In order to protect customer information, the Company has established a customer information management system, which focuses on organizational management and operation from the perspective of corporate strategy. Through the analysis of business procedures and information systems, the Company examines the access control of personal information acquisition, processing, transmission and storage, and discloses the privacy statement of customer information on the dealer’s website, which not only promises to protect customer privacy, but also clearly explains the use and security regulations of customer information to protect customer privacy. In 2022, the Company did not infringe customer privacy or received complaints by our customers on the infringement of their privacy.
Incident notification procedure
When an information security incident occurs, the unit(s) to which it occurred will notify the information security team— incident response team, determine the type of the incident, find the problem point, deal with it immediately, and leave a record.